The One Click That Could Ruin Your Vacation
Just because summer is winding down doesn’t mean the travel risks are. Whether you’re squeezing in one last vacation or planning a Labor Day escape, it’s good to stay alert. Cybercriminals are always looking for ways to exploit unsuspecting travelers, and falling victim is no way to close out your summer.
Scams like fake vacation rentals, bogus booking confirmations, and phony travel deals are common this time of year. They don’t just interrupt your plans. They can drain your wallet, compromise your personal information, and leave your devices vulnerable.
As your trusted tech team, we’re here to help you travel smarter and safer. In this post, we’ll cover the most common late-summer travel scams and how to protect yourself.
1. The Rise of Vacation Rental Scams
One of the most common and effective travel scams involves fake vacation rental listings. In fact, according to the FBI, consumers lost over $396 million to vacation rental scams in a single year.
Scammers often copy real listings from sites like Airbnb or VRBO and repost them with slight changes, hoping to lure in last-minute travelers.
The photos may look real, the descriptions may sound convincing, and the price might seem like a bargain. That’s exactly how they hook you.
How to Spot a Fake Listing Before You Book
Be cautious of anyone who asks you to pay outside the platform or rushes you to book. Secure payment methods and verified listings exist for a reason. Always communicate through the official site and be skeptical of vague or overly pushy messages. If something feels off, it probably is.
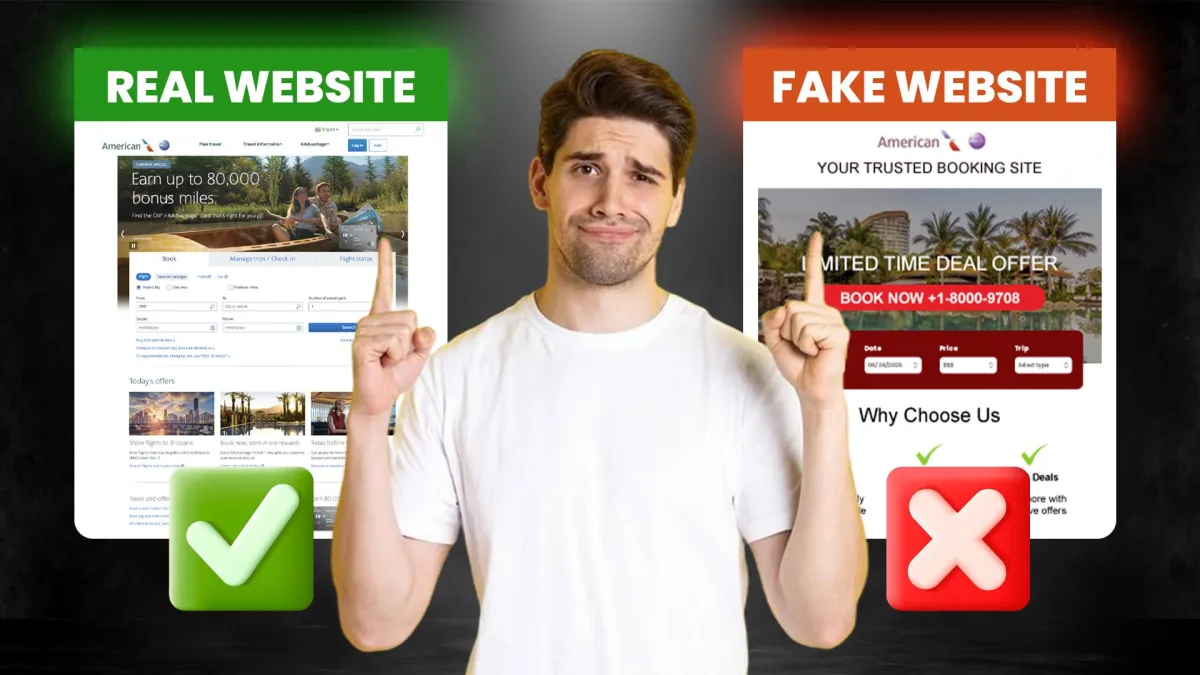
2. Fake Travel Booking Websites
When you’re in a hurry to find flights, hotels, or rental cars, it’s easy to click the first result that pops up in your search. Scammers know this, and they take advantage by creating fake booking websites that look almost identical to real ones.
Some fake sites appear in search results through paid ads or social media promotions. Others are sent through phishing emails pretending to be limited-time deals from trusted companies. Once you enter your information, the site might charge your card (and steal your info) without providing any services at all.
How to Avoid Fake Booking Sites
Double-check the URL before entering any personal or payment information. Scammers often use addresses that are slightly off; maybe a letter is missing, or it ends in “.net” instead of “.com.” It’s best to book directly through official travel company websites or apps whenever possible.
3. Phishing Emails Disguised as Itinerary Confirmations
Not every scam is easy to spot. Some of the most convincing ones show up in your inbox, disguised as emails from airlines, hotels, or travel apps. They may include your name, fake confirmation numbers, or even realistic-looking attachments to make the message feel legit.
These emails are designed to get you to click. The links may lead to fake login pages where your credentials can be stolen, or they could trigger malware downloads onto your device. Either way, they can cause real damage if you’re not careful.
How to Tell a Real Email from a Fake One
Before clicking anything, look at the sender’s email address closely. Many scam emails come from addresses that look official at a glance but are slightly altered.
Also, check for spelling errors, generic greetings like “Dear Customer,” and unusual urgency to act immediately. When in doubt, avoid clicking links and go directly to the company’s official website.
4. Fake Wi-Fi Networks at Hotels and Airports
Free Wi-Fi is a welcome convenience when you’re traveling, but it can also be a trap. Hackers often create fake networks that mimic the names of legitimate hotspots at airports, hotels, and cafes. These look like the real thing, but once you connect, the scammer may be able to monitor your activity or access sensitive information on your device.
This type of scam, sometimes called a “man-in-the-middle” attack, can expose your login credentials, financial details, and personal files without you even realizing it. It’s a quiet but serious threat that can follow you home long after your trip ends.
How to Stay Safe on Public Wi-Fi
If you need to use public Wi-Fi, avoid logging into sensitive accounts or entering payment information while connected. Use your phone’s mobile hotspot or a trusted VPN for added security when browsing on the go. It’s also wise to ask an employee at the location to confirm whether a network is legit before connecting.
5. Travel App Impersonators
When you’re preparing for a trip, it’s tempting to download apps that promise to streamline your travel experience. But not all apps are trustworthy. Some are designed to look like legitimate tools (such as booking platforms, maps, or itinerary organizers) but are actually fake.
These malicious apps can sneak onto your device and steal personal information, track your location, or even install malware. They often mimic the branding of real companies with slight name changes or fake positive reviews to appear more credible.
How to Avoid Malicious Travel Apps
Always download apps from official app stores like Google Play or the Apple App Store. Before installing, take a moment to review the developer’s name, read the reviews, and check how many downloads the app has. If something seems off or unfamiliar, look for an alternative.
Final Tips Before You Hit The Road
Travel should be about relaxation and making memories, not untangling financial fraud or fighting off malware. With just a few simple precautions, you can reduce your risk and enjoy a smoother trip from start to finish:
Keep your devices updated with the latest software and security patches.
Use strong, unique passwords for your travel accounts and enable multi-factor authentication.
Set up transaction alerts with your bank so you can spot suspicious charges right away.
Keep digital copies of important documents stored securely in the cloud or on a password-protected device.
Stay Safe and Enjoy the Rest of Summer
Cybercriminals don’t take vacations, but you still can. A little awareness goes a long way when it comes to protecting your personal information on the go.
By staying cautious, booking through trusted sources, and keeping your devices secure, you can avoid common travel scams and focus on what really matters: enjoying your getaway. And if anything feels off or you need help with the technical side of things, we’re always just a call or message away.
Stay safe, travel smart, and don’t hesitate to reach out if you have any questions.



